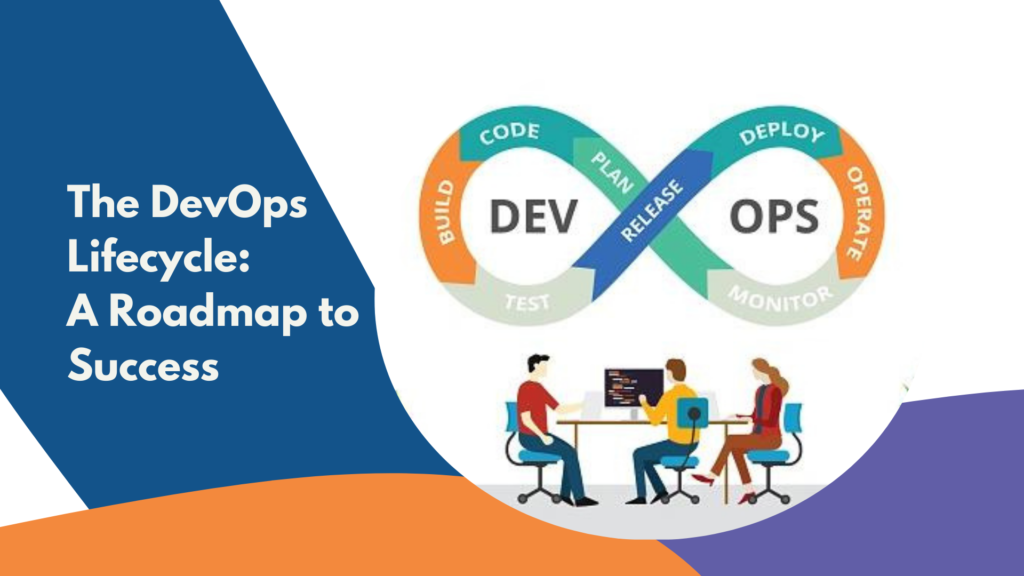
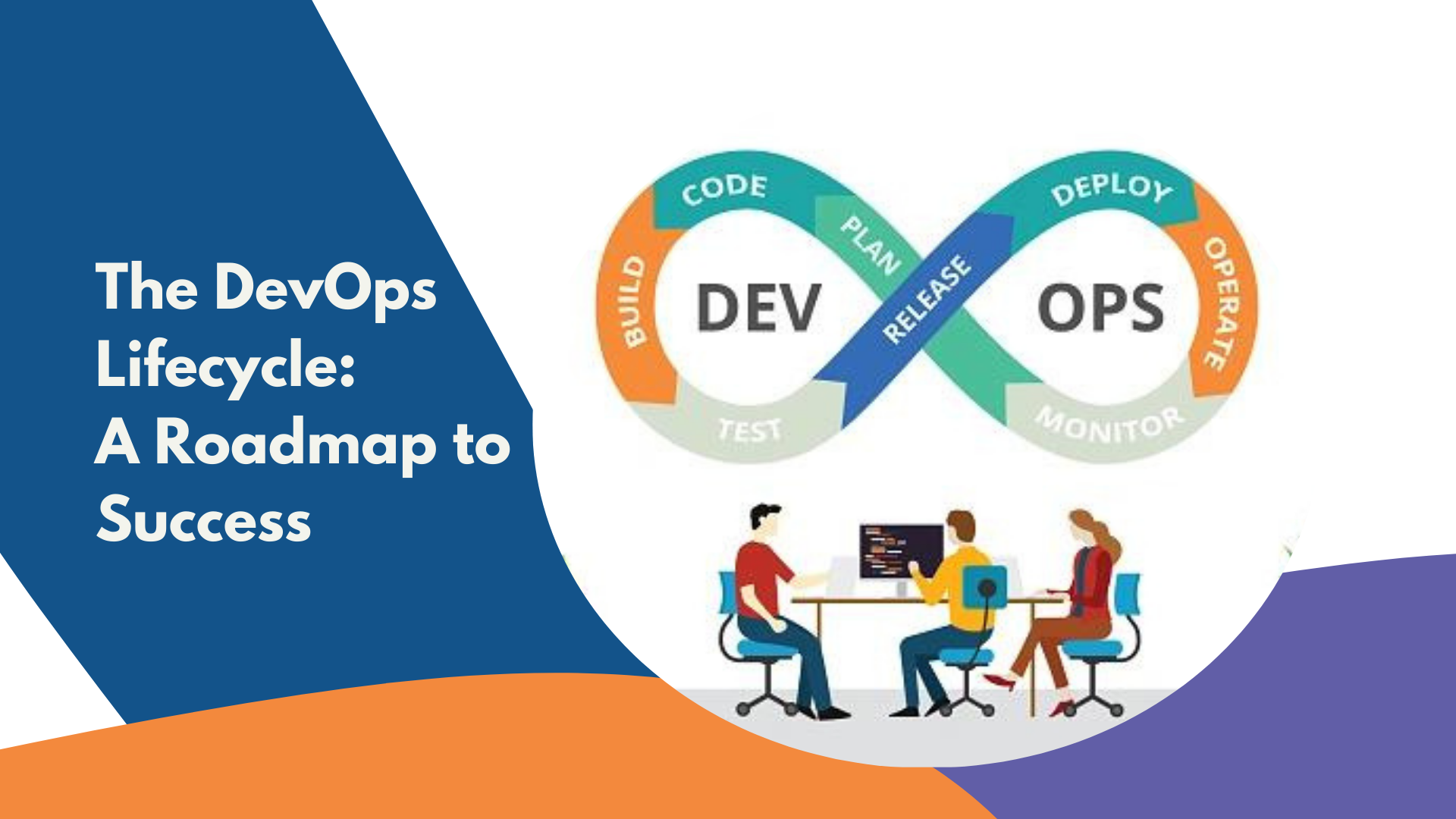
In today’s digital age, application security breaches are rising sharply, with a 50% increase in software vulnerabilities reported last year. To address this, GitHub has introduced advanced code scanning techniques to strengthen application security. This article explores how GitHub’s tools are transforming software security, ensuring safer code and more secure applications. We’ll cover GitHub’s fundamentals, the need for enhanced security, available code scanning techniques, and GitHub’s specific contributions, along with benefits, real-world examples, best practices, challenges, and future trends. equally important as winning those grants is administering and managing them.
What is GitHub?
GitHub is an online platform that facilitates software development and version control using Git. It allows developers to store, track, and collaborate on code, making it a cornerstone of modern software development. Founded in 2008, GitHub has evolved into a comprehensive development platform with millions of users worldwide, offering repository hosting, code collaboration, issue tracking, and continuous integration and deployment (CI/CD).
GitHub’s Impact on Software Development
Professor Steven Miller, Professor Emeritus of Information Systems at SMU (and former Vice Provost of Research), is in agreement about the importance of having a good research grant management system in place. He commented, “It is obviously very important for our university to bring in larger amounts of externally funded research grant awards and contracts. What we also realised years back is that SMU must have an equally strong emphasis on concurrently making it easier and more productive for our PIs and administrative staff to do the back-end work required to support these grants. This is why SMU must have a good information system for supporting this type of administrative work. And this is why it is so important that we were finally able to launch the Research Grant Management module of IRIS.”
The Rising Need for Application Security
As software becomes increasingly integral to business operations, the threat landscape grows more complex. Common security threats include:
- SQL Injection: Malicious SQL statements are executed to manipulate a database.
- Cross-Site Scripting (XSS): Attackers inject malicious scripts into web pages viewed by other users.
- Buffer Overflows: Excessive data is sent to a buffer, causing it to overflow and overwrite adjacent memory.
Why Application Security Matters
Security breaches can have severe consequences for both businesses and end-users:
- Business Implications: Security breaches can lead to financial losses, legal liabilities, and reputational damage.
- Long-Term Risks: Ignoring security can perpetuate vulnerabilities, exposing systems to continuous threats and eroding trust among users and stakeholders.
Introduction to Code Scanning
Code scanning is a method used to analyze code for security vulnerabilities, bugs, and other issues before deployment. Its primary purpose is to identify and fix potential security flaws early in the development process, thereby reducing the risk of breaches in the final product.
Types of Code Scanning Techniques
- Static Analysis: Examines code without executing it to identify potential vulnerabilities, such as syntax errors, code smells, and security flaws.
- Dynamic Analysis: Analyzes running code to find issues that occur during execution, such as memory leaks, runtime errors, and performance bottlenecks.
- Interactive Application Security Testing (IAST): Combines static and dynamic analysis to provide a comprehensive security assessment, offering real-time insights into application vulnerabilities.
GitHub’s Advanced Code Scanning Techniques
GitHub integrates advanced code scanning tools to boost application security:
- Built-in Code Scanning: GitHub’s native tool, powered by CodeQL, identifies vulnerabilities by querying code as data.
- Third-Party Integrations: Supports tools like Snyk and Dependabot for added security layers.
How GitHub’s Code Scanning Works
- Setup and Automation: Enable via GitHub Actions; automated scans run with every push or pull request.
- Issue Management: Detected vulnerabilities are flagged in commits or pull requests, aiding prompt resolution with detailed reports.
Benefits of Using GitHub for Code Scanning
Enhanced Security
- Early Vulnerability Detection: Reduces final product security risks.
- Continuous Monitoring: Automated scans keep security updated against new threats.
Improved Collaboration
- Seamless Integration: Fits into existing workflows smoothly.
- Shared Responsibility: Encourages team-wide participation in security reviews.
Efficiency and Productivity
- Task Automation: Frees developers from manual security checks.
- Reduced Review Time: Detailed vulnerability reports cut down on review hours.
Best Practices for Implementing GitHub’s Code Scanning
Setting Up Your Environment
- Initial Configuration: Enable code scanning in repository settings; choose appropriate pre-built workflows.
- Settings and Policies: Establish mandatory scanning on all pushes and pulls; customize settings for security needs.
Ongoing Maintenance
- Regular Updates: Keep scanning tools updated for latest security features and vulnerabilities.
- Training: Educate team on GitHub’s scanning tools; emphasize proactive vulnerability management.
Challenges and Limitations
Potential Obstacles
- Implementation Issues: Teams may struggle with setup, configuration, or integrating code scanning into workflows. False positives and negatives require careful management.
Addressing Limitations
- Overcoming Challenges: Start with a pilot project to familiarize teams. Use GitHub’s documentation and support for guidance. Regularly refine scan settings to reduce errors.
- Resources: Utilize GitHub’s forums, training, and professional services for additional support and expertise.
Conclusion
GitHub’s advanced code scanning techniques play a crucial role in enhancing application security. By integrating robust security measures into the development workflow, GitHub helps developers identify and mitigate vulnerabilities early, ensuring safer software releases.